Monday, August 31, 2009
Create The Perfect Web Experience With Load Testing
Create The Perfect Web Experience With Load Testing
Optimize Your Network Bandwidth With Network Monitoring
Electronic Network Solutions

Our network solutions for onboard electronics replace conventional electrics and bulky fixed wiring harnesses in vehicles. Featuring flexible multiplex architecture, our smart, state of the art networks offer high performance and reliable diagnostics. Drivers can access all relevant information at any time via a direct interface. Standard data buses enable easy connection of a variety of components.
Significantly reduce system costs
Our multiplexing onboard electronics system radically reduces the number of cables, connections, plugs, relays and fuses installed in a vehicle. This makes a major contribution to enhanced vehicle reliability and helps lower the cost of wiring activities, plus the time spent on quality checks, documentation and servicing. Alongside these savings, the costs associated with procurement, inventory and admin can also be trimmed.Computer N network

ChoiceOne computer and network consulting specializes in installation, administration, service and support of computer and network solutions to small and medium sized businesses. Serving the tri-state since 1997, ChoiceOne is committed to: network administration cost reduction, focused product knowledge and professional quality solutions.
Since its inception, ChoiceOne's ultimate goal is to increase the stability of your computer network using our network management formula. Through analysis, evaluation, configuration techniques and documentation we hope to reduce your support overhead requirements. Its is our hope and desire that through using ChoiceOne over the course of the year a reduction in billable hours will be the natural result. This has been the case with EVERY previous client utilizing our services.
Services available from ChoiceOne computer and networking consulting, Inc. are (but are not limited to).
1. Netware and Windows Server and Desktop Installation and support
2. Database Setup, Installation and Support
3. Networking Support
4. Hardware/Software Support
5. Internet/Intranet Security
6. Disaster Recovery
7. Internet Consultation, Installation and Support
8. E-mail System Design and Installation
9. Documentation
10.Network Design
11.Internet Firewall
12.Network Operating Fault Isolation
13.System Administration
14.Training
15.Computer Network Cabling
16.Office Phone Systems.
Quality Network Solutions
 San Francisco Computer Repair's staff of support specialists, on-site field engineers, and certified consultants are highly skilled professionals. Each will give you the support needed to successfully maintain your mission-critical network. Your call will be answered directly by your assigned support specialist or call coordinator. Your assigned support specialist will direct your support issues from beginning through to the best resolution. San Francisco Computer Repair's established call-tracking system allows our service manager to follow the progress of your call to its decisive resolution. Every step of every calls have a built-in time frame for completion of the task, which helps them ensure that your needs are quickly accomplished. Web Sites, Domain Names, and Hosting - We do it all. Network solutions for today's information technology.
San Francisco Computer Repair's staff of support specialists, on-site field engineers, and certified consultants are highly skilled professionals. Each will give you the support needed to successfully maintain your mission-critical network. Your call will be answered directly by your assigned support specialist or call coordinator. Your assigned support specialist will direct your support issues from beginning through to the best resolution. San Francisco Computer Repair's established call-tracking system allows our service manager to follow the progress of your call to its decisive resolution. Every step of every calls have a built-in time frame for completion of the task, which helps them ensure that your needs are quickly accomplished. Web Sites, Domain Names, and Hosting - We do it all. Network solutions for today's information technology.
Saturday, August 29, 2009
Network Topology Diagrams
Main Types of Network Topologies In networking, the term "topology" refers to the layout of connected devices on a network. This article introduces the standard topologies of computer networking.
One can think of a topology as a network's virtual shape or structure. This shape does not necessarily correspond to the actual physical layout of the devices on the network. For example, the computers on a home LAN may be arranged in a circle in a family room, but it would be highly unlikely to find an actual ring topology there.
Network topologies are categorized into the following basic types:
Star Topology
Ring Topology
Bus Topology
Tree Topology
Mesh Topology
Hybrid TopologyMore complex networks can be built as hybrids of two or more of the above basic topologies.
Star Topology Many home networks use the star topology. A star network features a central connection point called a "hub" that may be a hub, switch or router. Devices typically connect to the hub with Unshielded Twisted Pair (UTP) Ethernet.
Compared to the bus topology, a star network generally requires more cable, but a failure in any star network cable will only take down one computer's network access and not the entire LAN. (If the hub fails, however, the entire network also fails.)
See the illustration of Star Network Topology.
Advantages of a Star Topology

Easy to install and wire.
No disruptions to the network then connecting or removing devices.
Easy to detect faults and to remove parts.
Disadvantages of a Star Topology
Requires more cable length than a linear topology.
If the hub or concentrator fails, nodes attached are disabled.
More expensive than linear bus topologies because of the cost of the concentrators.
The protocols used with star configurations are usually Ethernet or LocalTalk. Token Ring uses a similar topology, called the star-wired ring.
Star-Wired Ring
A star-wired ring topology may appear (externally) to be the same as a star topology. Internally, the MAU of a star-wired ring contains wiring that allows information to pass from one device to another in a circle or ring (See fig. 3). The Token Ring protocol uses a star-wired ring topology.
Ring Topology In a ring network, every device has exactly two neighbors for communication purposes. All messages travel through a ring in the same direction (either "clockwise" or "counterclockwise"). A failure in any cable or device breaks the loop and can take down the entire network.
To implement a ring network, one typically uses FDDI, SONET, or Token Ring technology. Ring topologies are found in some office buildings or school campuses.
BUS NETWORK

Ethernet bus topologies are relatively easy to install and don't require much cabling compared to the alternatives. 10Base-2 ("ThinNet") and 10Base-5 ("ThickNet") both were popular Ethernet cabling options many years ago for bus topologies. However, bus networks work best with a limited number of devices. If more than a few dozen computers are added to a network bus, performance problems will likely result. In addition, if the backbone cable fails, the entire network effectively becomes unusable.
Easy to connect a computer or peripheral to a linear bus.
Requires less cable length than a star topology.
Disadvantages of a Linear Bus Topology
Entire network shuts down if there is a break in the main cable.
Terminators are required at both ends of the backbone cable.
Difficult to identify the problem if the entire network shuts down.
Not meant to be used as a stand-alone solution in a large building.
Thursday, June 18, 2009
Wireless network interface card

A wireless network interface controller (WNIC) is a network card which connects to a radio-based computer network, unlike a regular network interface controller (NIC) which connects to a wire-based network such as token ring or ethernet. A WNIC, just like a NIC, works on the Layer 1 and Layer 2 of the OSI Model. A WNIC is an essential component for wireless desktop computer. This card uses an antenna to communicate through microwaves. A WNIC in a desktop computer usually is connected using the PCI bus. Other connectivity options are USB and PC card. Integrated WNIC's are also available, (typically in Mini PCI/PCI Express Mini Card form).
Contents
1 Modes of operation
2 Range
Modes of operation
A WNIC can operate in two modes known as infrastructure mode and ad hoc mode.
In an infrastructure mode network the WNIC needs an access point: all data is transferred using the access point as the central hub. All wireless nodes in an infrastructure mode network connect to an access point. All nodes connecting to the access point must have the same service set identifier (SSID) as the access point, and if the access point is enabled with WEP they must have the same WEP key or other authentication parameters.
In an ad-hoc mode network the WNIC does not require an access point, but rather can directly interface with all other wireless nodes directly. All the nodes in an ad-hoc network must have the same channel and SSID.
WNICs are designed around the IEEE 802.11 standard which sets out low-level specifications for how all wireless networks operate. Earlier interface controllers are usually only compatible with earlier variants of the standard, while newer cards support both current and old standards.
Specifications commonly used in marketing materials for WNICs include:
Wireless data transfer rates (measured in Mbit/s); these range from 2 Mbit/s to 54 Mbit/s.[1]
Wireless transmit power (measured in dBm)
Wireless network standards (may include standards such as 802.11b, 802.11g, 802.11n, etc.) 802.11g offers data transfer speeds equivalent to 802.11a – up to 54 Mbit/s – and the wider 300-foot (91 m) range of 802.11b, and is backward compatible with 802.11b.
Wireless local area network standards view • talk • edit 802.11
Protocol Release[2] Freq.
(GHz) Typ throughput
(Mbit/s)
[citation needed] Max net bitrate
(Mbit/s) Modulation rin.
(m) rout.
(m)
– Jun 1997 2.4 00.9 002 DSSS ~20 ~100
a Sep 1999 5 23 054 OFDM ~35 ~120
b Sep 1999 2.4 04.3 011 DSSS ~38 ~140
g Jun 2003 2.4 19 054 OFDM ~38 ~140
n Nov 2009 2.4
5 130[3] 600[4] OFDM ~70 ~250[5]
y Nov 2008 3.7 23 054 OFDM ~50 ~5000
RANGE
Wireless range may be substantially affected by objects in the way of the signal and by the quality of the antenna. Large electrical appliances, such as a refrigerators, fuse boxes, metal plumbing, and air conditioning units can impede a wireless network signal. The theoretical maximum range is only reached under ideal circumstances and true effective range is typically about half of the theoretical range.[1] Specifically, the maximum throughput speed is only achieved at extremely close range (less than 25 feet (7.6 m) or so); at the outer reaches of a device's effective range, speed may decrease to around 1 Mbit/s before it drops out altogether. The reason is that wireless devices dynamically negotiate the top speed at which they can communicate without dropping too many data packets.
Thursday, June 4, 2009
Networking Topologies

An Overview of Computer Network Topology
Network topology is one of the very important topics to learn when it comes to build up computer network. There are many Network Topologies on which network administrator decide to build the network on. Topology is basically defined as layout or design of network, and computers are connected using the design of the topology. These topologies can be either physical or logical design. Physical topology refers to physical design of network which includes devices, cables, location and installation of network where as in logical topology it is the amount of data to be transferred with in the network as apposed in its design.
There are five different Networking Topologies :
a) Bus
b) Star
c) Ring
d) Mesh
e) Tree.
When networks are design using multiple topologies it is called Hybrid Networks, this concept is usually utilized in complex networks were larger number of computer clients are required.
Bus Topology:
Bus topology is one the easiest topologies to install, it does not require lots of cabling. There are two most popular Ethernet cable types which are used in this topology they are 10Base-2 and 10BaseT. Bus topology based networks works with very limited devices. It performs fine as long as computer count remain with in 12 – 15, problems occurs when number of computer increases.
Bus topology uses one common cable (backbone) to connect all devices in the network in linear shape. Network interface cards of all network devices are attached to single communication medium backbone cable. When any computer sends out message in the network it is broadcasted in the entire network but only intended computer accepts the message and process it. Bus topology provide simplicity to the network, however there is big disadvantage of this topology, if main single network cable some how gets damaged, it will shut down the entire network no computer will run on network and no communication can be made among computers until backbone cable is replaced.
Ring Topology:
Ring topology is one of the old ways of building computer network design and it is pretty much obsolete. FDDI, SONET or Token Ring technologies are used to build ring technology. It is not widely popular in terms of usability but incase if you find it any where it will mostly be in schools or office buildings. In ring network topology computers and other networking devices are attached to each other in such a way that they have devices adjacent to each other (Left and right side). All messages are travelled in the same directory either clockwise or anticlockwise. In case of failure of any device or cable the whole network will be down and communication will not be possible.
Star Topology:
This is the most commonly used network topology design you will come across in LAN computer networks. In Star, all computers are connected to central device called hub, router or switches using Unshielded Twisted Pair (UTP) or Shielded Twisted Pair cables.
In star topology, we require more connecting devices like routers, cables unlike in bus topology where entire network is supported by single backbone. The most practical point of Star topology success is that the entire network does not go down incase of failure of a computer or cable or device, it will only affect the computer whose wire failed rest of the network will be working fine. However, incase of failure of central communication device such as Hub, Router or Switch the entire network will collapse. Star topology is widely used in homes, offices and in buildings because of its commercial success.
Tree Topology:
Just as name suggest, the network design is little confusing and complex to understand at first but if we have better understanding of Star and Bus topologies then Tree is very simple. Tree topology is basically the mixture of many Star topology designs connected together using bus topology. Devices like Hub can be directly connected to Tree bus and each hub performs as root of a tree of the network devices. Tree topology is very dynamic in nature and it holds potential of expandability of networks far better than other topologies like Bus and Star.
Mesh Topology:
Mesh topology is designed over the concept of routing. Basically it uses router to choose the shortest distance for the destination. In topologies like star, bus etc, message is broadcasted to entire network and only intended computer accepts the message, but in mesh the message is only sent to the destination computer which finds its route it self with the help of router. Internet is based on mesh topology. Routers plays important role in mesh topology, routers are responsible to route the message to its destination address or computer. When every device is connected to every other device it is known as full mesh topology and if every device is connected indirectly to each other then it is called partial mesh topology.
Conclusion:
Topologies are essence of computer networks design. Efficent networks can only be built based on the complete knowledge and understanding of above mentioned topologies. Knowledge of every communication device is of equal importance to help you find the best option for your network requirements. Optimum networks can be built with complete knowledge and understanding of computer network devices and how they are designed, any mistake in choosing inappropriate techniques, device etc can only be the waste of time, resources
Network Design and Implementation
There is a perception that LAN design is very simple and straightforward, and that a single solution will fit almost any scenario. This is where most LAN-related problems originate. To build a well-balanced LAN, a number of factors must be taken into consideration. Some of them are: desired network size (# of machines), layout, amount of current traffic, future traffic expectations, security requirements. We evaluate all of these factors, among others, which helps us design a flexible solution within budget, and with sufficient room for expansion.
Remote Network Solutions
When a company has several offices, remote connectivity is essential. In most cases, communicating only via email is far from adequate. File sharing, Windows domain-based services, and direct access between workstations are often needed. To achieve this, we build virtual tunnels between your offices, as well as to our own network. Machines in separate locations can now communicate as if they were on the same physical network. And for those working at home or on the road, we provide easy VPN access to the office network.
Centralized Routing
We handle all routing at the core of our network. If you have several locations, we will interconnect them with redundant virtual links. In case one of those links becomes unavailable, our dynamic routing protocols automatically send traffic via the remaining ones. In the meantime, our network engineers are notified of the situation and start working on the problem immediately. Having multiple paths brings peace of mind to our customers and us.
Network Redundancy
For critical applications, a single-sided network may not be adequate. Designing redundant systems is one of our specialties. We can set up router and switch redundancy with failover, up to a full network mesh. In case any one device fails, connectivity is not affected. In addition, we are able to utilize multiple Internet links, if available. They can be used in an active-standby scenario, or an active-active one. Load-balancing solutions play an important role in networking, and we take full advantage of what today’s technology offers.
Network Security

Detecting and preventing intrusion with deep packet analysis and forensics
Today's enterprise organizations rely on digital assets that must be protected from unauthorized access or dispersion. The costs of data leakage are well documented and include not only loss of value, intellectual property and customers, but also government sanctions and fines for noncompliance to data privacy regulations. A complete deep packet capture, record and playback solution from Solera Networks ensures that the source of data leaks are quickly identified, stemming the loss of data.
With easy packet level reconstruction of all of the traffic on your network, you now have context for what happened before, during and after every security alert.
A capture appliance from Solera Networks gives all of your securtiy tools, whether they be Intrusion Detection, Intrusion Prevention, or Firewalls, full context into what has happenned on your network.
Network Security »Tuesday, May 5, 2009
Wireless LAN (WLAN)
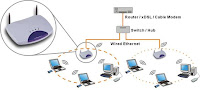
Digi - Wireless Device Networking

"...device networking for business, develops reliable products and technologies to connect and securely manage local or remote electronic devices over the network or via the web."
Wi-Fi - 802.11a/b/g Wireless LAN Networking -
External and embedded Wi-Fi products make it easy to add embedded 802.11a/b/g wireless LAN networking to any electronic device, or to connect serial devices over a Wi-Fi network.
Network Cable Tester, LAN Tester
 Detailed Product Description
Detailed Product DescriptionSpecifications:
This LAN tester for different cable types is indispensable in network installation and maintenance.
This compact device can be used for testing network.
Telephone (rj-45 rj-11 rj12) and most types of computer cable
----LED indication
----advanced design for easy testing
----ability to test cables from a distance and in places that are not easily accessible
----automatically runs all tests and checks for continuity, open, shorted and crossed wire pairs
----switch can automatic shut when open 2-3 minute
----tests: rj-45, 10 base-t, token ring, rj11 / 12 cable
----power supply supply 9v-battery (not incl)
Network Server
 Detailed Product Description
Detailed Product DescriptionA. Network Attached Storage
Multiple users can access the same storage device to share and exchange files. Simply connect up to two USB drives to the M-DM Download Manager, set up a shared folder and let users access the files via local network connection using SMB or FTP.
B. Printer sharing
No need to connect the printer to a specific computer, only need to connect it to this product and this product should be in Local area network, then, all of the computer in the Local area network can use this printer
C. FTP server
The FTP utility on the Mac will be able to read the data on the network storage but you can not write new data to the drive. To do that,you will need to install a dedicated FTP application,which can either be a free utility or professional shareware programs.
Outside Hard drive as a FTP Server, any user who knows IP ID or Password of this products can download the shared data on the hard disk through internet.
Function is similar with some companies which download product data with long-distance.
D. Support BT or other download method
MDT-LS201 Download Manager allows you to put up to ten Torrent files in to a queue, and will download two at a time, to maximise the speed of the download. As soon as one download is finished, the next one will automatically start. If one download is for any reason broken off, the Download Manager will go on to the next download and try that one again later. You can then turn off your computer and go about other things (like sleeping!) and when you come back, you will have all kinds of new media files to enjoy.
After setting the download contents to this product on PC, then, close the PC, this product also can work for long time or finish download task independently.
User group can focus on SOHO crowd, you can download Electronic book or film, or other documents with it when no power on computer.
F. USB OTB Copy
The USB copy function can be used to copy data from one USB storage device to another.Simply connect both drives,tum them on and press the copy button to start the process.In general,the source is on port B and the destination is on port A but there are a couple of exceptions.
The copy function will copy all data stored on the source drive,create a new folder on the destination drive with the current time and then paste the files into that newly created folder.
G. Universal Plug and Play (UPnP is only available on request)
The MDT-LS201 Download Manager supports UPnP v1.0. If you have other devices that can access UPnP storage devices,you will be able to share your files on the attached USB drives in the local network via UPnp
There is no need to configure anything,this function is turned ON by default and other devices will be able to recognise it automatically.
Ø Up to two external USB storage drives
Ø Interface/Ports 10/100Base-TX Auto MDI/MDI-X, 1 port (RJ-45)
Ø USB 2.0 High Speed (USB1.1), 2 upstream ports (Type A)
Ø Half-Duplex and Full-Duplex operation
Ø TCP/IP (UPnP available on request)
Ø Up to 8 simultaneous connections
Ø DHCP Setup, Auto IP, Fixed IP, System Time (NTP)
Ø Setup for Accounts, Status, Access Right and User Setup, Share Level Access
Ø Input: AC 100-240V, 0.6A, 50-60Hz
Ø Output: DC +5V/2A
Product Size 133mm x 8.0mm x 2.0mm
Saturday, May 2, 2009
Firewall

- Packet filtering firewall
- Circuit level firewall
- Application level firewall
- Stateful inspection firewall
A packet filtering firewall is a router or computer (with special software) which screens incoming and outgoing packets. It reads information contained in each packet's TCP and IP headers then accepts or denies the packets based on the rules it has configured. Typically, it looks at rules based on the source address, the destination address, the application, the protocol, the source port number, or the destination port number. A packet filtering firewall operates only in the network layer of the OSI model.
A circuit level firewall monitors TCP handshaking between packets from trusted clients or servers to untrusted hosts to determine if the session is legitimate. A circuit level gateway checks the handshaking occurring with the synchronize (SYN) and acknowledge (ACK) packets in TCP. Since these packets occur at certain times and in a certain order, the circuit level gateway determines if they are operating correctly before allowing the communication. This type of firewall operates at the session layer of the OSI model.
An application level firewall operates a proxy between internal and external machines. It intercepts incoming and outgoing packets and copies and forwards the information to the destination addresses. The application level firewall acts as a proxy for the services it can proxy. For example, you can setup an application level firewall to proxy http and telnet requests - if you do not have it configured to proxy FTP requests, those would get dropped. An application level firewall checks packets up through the application layer of the OSI model.
A stateful inspection firewall combines aspects of the previously described firewalls. It operates at the network layer of OSI model, filtering all incoming and outgoing packets based on source, destination IP address, and port numbers. It also functions as a circuit level firewall by determining which packets in a session are appropriate. A stateful inspection firewall can also mimic an application level gateway in the application layer. A stateful inspection firewall is one of the most common firewalls as it combines features of the first three types.
Transceiver

A Transceiver, or media converter, is a device which interfaces between the network and a local node. An example of a transceiver is an MAU. A transceiver generally converts to different types of connectors, like AUI and RJ-45.
An MAU is a media attachment unit - a device which connects the computer to the Ethernet network.
A transceiver works at the Physical layer (layer 1) of the OSI model.
Modem

A Modem is a device which enables a computer to transmit data over analog telephone lines. Modem is short for modulator-demodulator. A modem converts the digital information in a computer into analog data. Traditional modems can operate at a top speed of 56Kbps, though most do not go that fast on today's phone lines.
A lot of companies still rely on dial-up access using modems for connectivity, though companies are increasingly moving to other methods of connectivity including cellular modem cards and high speed Internet access (such as DSL or cable modem).
A modem operates in the Physical Layer (layer 1) of the OSI model.
ISDN Adapter

A Wireless Access Point (WAP) is a transceiver or radio component in a wireless LAN that acts as the transfer point between wired and wireless signal and vice versa. The access point connects the wired LAN to an antenna. It bridges the wired and wireless networks together.
A Wireless Access Point operates in layer 3 of the OSI model.
CSU/DSU

Friday, May 1, 2009
Gateway
Router

A Router is a device that determines the next point a data packet needs to be forwarded to on to its destination. The router is connected to more than one network and determines where each data packet should be sent based on its current understanding of the networks it is connected to. Routers have table which shows the available routes and decides based on this table what the best route is for a given packet of information.
A router operates in level 3 of the OSI model.
If you have a cable modem or DSL modem at home, you probably have a router between your internal network and Internet.
Bridge
 A Bridge is a networking device which connects multiple LANs and forwards or filters data packets between them based on their destination address. Bridges operate at the data link (level 2) of the OSI model.
A Bridge is a networking device which connects multiple LANs and forwards or filters data packets between them based on their destination address. Bridges operate at the data link (level 2) of the OSI model.Bridges are most frequently used to connect LAN segments to other LAN segments or to a wide area network (WAN). Bridges are protocol independent, you could connect an Ethernet network with a Token Ring network using a bridge. Typically though, they are used to connect two similar networks together.
HUB

A Hub connects all the nodes of a network using Twisted Pair (UTP or STP) cables. In a Hub, the signals received on one port are transmitted to all other ports, and vice versa. All nodes (work stations) connected using a Hub can listen to one another all the time. The advantage of using a Hub is low cost, and easy integration. The disadvantage is reduced bandwidth, and data security. The reduction in bandwidth comes due to the fact that all workstations are in the same collision domain. If two or more workstations try to transmit during the same time, it results in collision of signals, and the signals are lost altogether. As a result, the available bandwidth of the Ethernet network is reduced.
Network Interface Card(NIC)

The Network Interface Card (NIC) used connect the computer to the external network. It will normally have a PCI connector (Edge connector) to connect to one of the PC expansion slots, and an RJ-45 connector to connect to external Ethernet. Note that the interface connectors may differ depending upon the expansion bus being used (for example, PCI, ISA, EISA, USB etc.), and the networking media being used (for example, 10Base2, 10Base5, 10BaseT, etc.). Each of these have their own interface specifications. Almost all NICs have LED indicators showing the network connectivity.
Wireless Access Point

A Wireless Access Point (WAP) is a transceiver or radio component in a wireless LAN that acts as the transfer point between wired and wireless signal and vice versa. The access point connects the wired LAN to an antenna. It bridges the wired and wireless networks together.
A Wireless Access Point operates in layer 3 of the OSI model.
Using Wireless Routers on ResNet
Many students have more than one network device (desktop, laptop, video game consoles, handheld devices, etc) they wish to use on the network simultaneously. However, ResNet only has enough available IP addresses to allow one network connection per student. So, you can either alternate which network device you currently have registered by editing Your Account (link on left sidebar) or you can use a network router.
Router Basics
A router is a network device allowing multiple computers, handheld devices and game consoles to communicate with each other and share a single connection to the Internet. They usually contain one uplink (WAN) jack and between 4 and 24 ethernet (LAN) jacks where network devices can be plugged in. By connecting a router in the correct way to ResNet, multiple network devices can share the same connection.
Securing Your Wireless Router
ResNet requires you to secure your wireless router to use it on ResNet. You must use wireless encryption, which encodes the data transmitted between your PC and your wireless router. Unfortunately, most routers ship with encryption turned off, leaving it completely exposed. Enable your router's encryption and use the strongest form supported by your comptuer. The Wireless Protected Access (WPA) protocol and more recent WPA2 have supplanted the older and less-secure Wireless Encryption Protocol (WEP).
network service

We can create a custom quote for your business based on the following services:
Campus Network Design
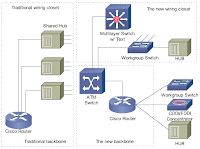
Network Design


Network Design and Implementation
 Local Area Networks
Local Area Networks Remote Network Solutions
When a company has several offices, remote connectivity is essential. In most cases, communicating only via email is far from adequate. File sharing, Windows domain-based services, and direct access between workstations are often needed. To achieve this, we build virtual tunnels between your offices, as well as to our own network. Machines in separate locations can now communicate as if they were on the same physical network. And for those working at home or on the road, we provide easy VPN access to the office network.
For critical applications, a single-sided network may not be adequate. Designing redundant systems is one of our specialties. We can set up router and switch redundancy with failover, up to a full network mesh. In case any one device fails, connectivity is not affected. In addition, we are able to utilize multiple Internet links, if available. They can be used in an active-standby scenario, or an active-active one. Load-balancing solutions play an important role in networking, and we take full advantage of what today’s technology offers.




